Traceable AI Protects Against the Log4j / Log4Shell Vulnerabilities


[et_pb_section fb_built="1" admin_label="section" _builder_version="4.16" custom_padding="0px||||false|false" global_colors_info="{}"][et_pb_row admin_label="row" _builder_version="4.16" background_size="initial" background_position="top_left" background_repeat="repeat" global_colors_info="{}"][et_pb_column type="4_4" _builder_version="4.16" custom_padding="|||" global_colors_info="{}" custom_padding__hover="|||"][et_pb_text admin_label="Text" _builder_version="4.23" background_size="initial" background_position="top_left" background_repeat="repeat" hover_enabled="0" sticky_enabled="0"]A new and severe vulnerability (CVE-2021-44228), dubbed "Log4Shell", has been identified in the widely used Apache Log4j Java logging package which gives the attacker the ability to run unauthenticated remote code execution on a targeted server. This vulnerability is actively being exploited. Well-known web services and applications such as Apple iCloud, Twitter, Amazon, Baidu, and Minecraft are reported to have all been targeted.Log4j is a very popular package used by many popular web services, websites, enterprise applications, and client software. The potential impact of this vulnerability is widespread and far-reaching. Teams from all over the Internet are “all hands on deck” today figuring out how to manage and mitigate the risk of this vulnerability.There is now a patched Log4J version (2.15.0) available and anyone using Log4J should upgrade to it as soon as possible. There are also a few other identified mitigations that can be put in place. However, library changes and configuration or code changes might not be something that every organization is in a position to do or to do quickly. And given the severity and reach of this vulnerability, having a layered defense strategy is a good idea.
Traceable AI can protect you immediately, at no cost
A layer of protection against these new Log4Shell attacks can and should be set up at the API & application traffic layer. The Traceable AI free API & app security solution can shield you from related exploits while the updates and patches are applied. Without requiring any configuration changes, library updates, or code changes to your application you can get a constant guard, immediately detecting and protecting against Log4j RCE exploits and other types of known and unknown attacks.


More Than Just Protection . . . Discovery
Besides detecting and blocking Log4Shell exploits, a natural question will certainly be “where are we exposed?” True this can be partially found by searching through the code you know is being used. But what about the code for the services that you don’t know about? And what about the services that you don’t have code for?Traceable AI provides you a continuously updated live API catalog of all the APIs being used between all the services in your application landscape. This includes which APIs are talking to which services (what we call your application flow). Having a complete live API catalog means that you can quickly see if any calls are being made to Log4J services. This visibility can also help you find zombie and shadow APIs, some of which might also be calls to the vulnerable Log4J package.
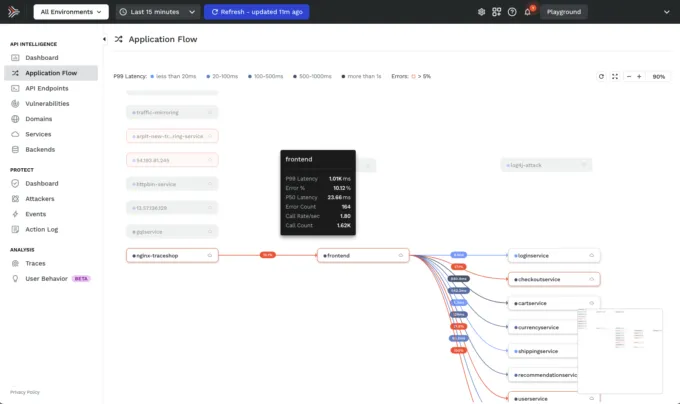
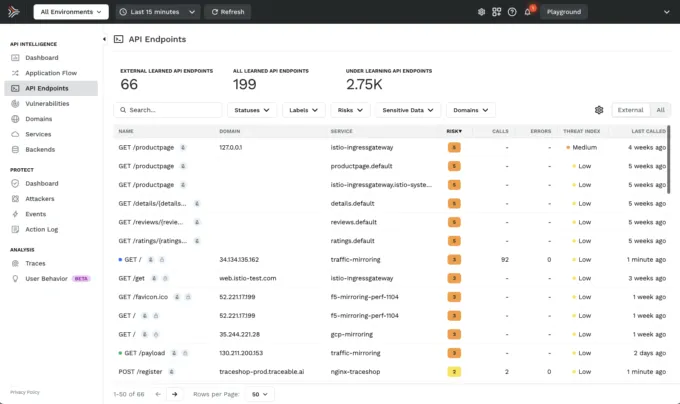
Security Observability
Traceable AI can help with new exploits (like those based on Log4Shell) in other ways than just detecting, blocking, and discovering. Traceable AI is a full security observability platform and watches all your application & API traffic for user and API behavior anomalies. It then records all the details about the chain of transactions (called traces). If a Log4Shell attack does happen, Traceable AI can tell you where it happened from, what user did the attack (not just what IP), what their attack history looks like over time, which services were attacked or used along the way to the attack point, what sensitive data might have been compromised, and so much more. All this correlated data can help you to do forensics, threat hunting, and figure out potential collateral damage.
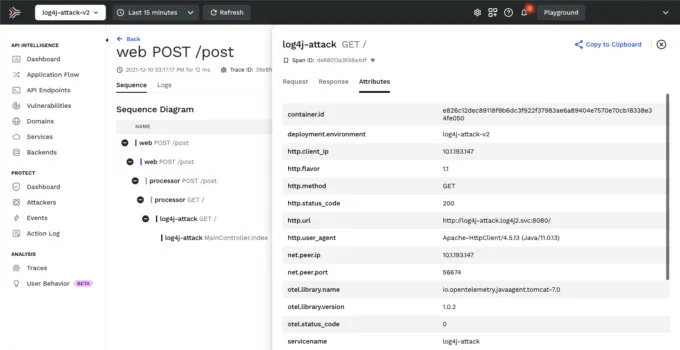
Raise the Shields!
This new Log4Shell vulnerability needs immediate attention and has security, operations, and app teams working under pressure to protect their applications as quickly as possible. A good multi-pronged strategy can be to reduce the pressure by shielding immediately, while library updates and any necessary code and configuration changes are tested and put into place.Getting an intelligent API & application security tool in place, such as Traceable AI, can not only help reduce the likelihood of damage from the new Log4Shell vulnerability but also potentially help protect your applications from the next unknown zero-day vulnerability that comes along.[/et_pb_text][/et_pb_column][/et_pb_row][/et_pb_section]
The Inside Trace
Subscribe for expert insights on application security.
.avif)




