What is Web Application Security?


Web Application Security is security for web apps, right? Ensure the application and data are available when needed to the users who are authorized to see and use it (and only those users). Definition done. Move on.
But there’s more to it. As with many technical topics, there are plenty of rabbit holes to dive into when discussing web application security, but let’s focus on the critical questions many have about it.
- Why is web app security important?
- What processes are necessary to implement it well?
- Does it hurt the user experience?
- How do I get started implementing such an overwhelming program?
Why is Web Application Security Important?
The answer to this question may seem obvious, but when faced with the day-to-day tasks of helping our organizations become more secure, the “why” can get lost.
Web applications are growing in number and usage. The COVID-19 pandemic has forced businesses to improve or create their online presence to survive. The number of web applications and APIs makes them a tempting target for attackers. These web applications also hold a growing amount of our sensitive data.
Here are some stats that we found surprising and reinforce our desire to protect modern web applications:
- Someone attacks your websites about every 39 seconds on average - your site isn’t immune to threats
- 60.5% of vulnerabilities found in 2019 were remotely exploitable - an attacker doesn’t have to be anywhere near you to exploit vulnerabilities and steal data
- 42% of vulnerabilities in Internet-facing applications are SQL injection errors - SQL injection was first discovered in 1998 and is still going strong
- 82% of vulnerabilities are in application code - network security isn’t good enough anymore
The changing face of application development has increased many web applications’ attack surface, and code errors still pop up.
We need web application security now more than ever before. However, putting it into practice can be challenging for organizations.
How Do You Secure a Web Application?
Web application security is an enormous discipline with three areas of impact within your organization: people, processes, and technology.
People
Application security is impossible without all hands on deck helping to keep your data safe. Training is essential to helping employees understand the importance of security and how to apply it to their jobs.
For example, customer service representatives should know what information they’re allowed to give out without extra authentication. Don’t tell sensitive data to anyone who calls. Help them understand that social engineering customer service representatives take over accounts or steal identities is a common attack vector. Help them develop a “trust but verify” approach to handling customer calls.
Penetration testers are another invaluable group of people. They learn real-world attack scenarios and use them against your application to find vulnerabilities before the bad guys do. While many companies outsource penetration testing, a growing number of organizations are forming “red teams” -- internal teams that regularly perform security assessments to make sure new vulnerabilities aren’t creeping into applications over time.
Finally, a good team of application security experts is needed to educate developers about secure coding practices. Finding security talent isn’t easy, but it’s worth the investment. Also, don’t be afraid to bring on those enthusiastic about security, even if they aren’t as experienced. Nurture the talent you need, and you’ll reap the rewards for years to come.
Processes
Once the right people are in place and trained, it’s time to develop processes they can use to keep track of your applications’ health. An airline pilot has a pre-flight checklist they use to make sure it’s safe to take off. They know that skipping steps on the list could have dire consequences for passengers.
Similarly, application security checklists are necessary so you can have confidence in the safety of your customers’ data. Following a consistent process makes sure you don’t miss anything.
What items should you include in your checklist?
Pre-production
First, code review is an essential development practice. Not every developer understands security, so not every review is a hardcore assessment of code vulnerabilities. However, your organization has standards of development that the security team helped create. During code reviews, developers should ensure the code is following those guidelines.
Next, keep track of the open-source and third-party software you’re using. There are many software solutions available that scan your code’s dependencies to build an inventory of what you’re using and whether it’s out of date or vulnerable to critical security bugs.
Risk management is the process of cataloguing business risks and mitigating them to the proper degree. And while it’s a topic that could fill a book on its own, risk management is an essential part of web application security. For example, understanding which public APIs handle personally identifiable information (PII) informs many decisions. You wouldn’t necessarily need to shut down such a service, but you would put pieces in place to prevent the theft and misuse of PII.
Threat modeling is the practice of reviewing an application’s architecture and data flow to determine likely threats against it. For example, a threat against a financial application would be an attacker intercepting a transaction and rerouting the money to their account instead of the intended recipient. Another danger could be the theft of passwords or personally identifiable information. Threats are rated according to severity, and remediation is done through application design or refactoring.
Production
Finally, monitoring and defending is an essential web application security process. You should know what is happening within your application and why through logging centralization or real-time tracing of your API calls. Effective monitoring allows you to react quickly to problems or attacks and reduce the damage of each incident.
The processes required to secure your web applications take time and effort to create and perfect. Solid monitoring and defensive capabilities in production should be your first priority to provide cover while putting the other processes in place.
Throughout Product Lifecycle
Vulnerability management is the practice of managing application vulnerabilities through the lifecycle of discovery to remediation. You can discover vulnerabilities through threat modeling, penetration testing, automated scans, and real-world attacks. Issues found should be prioritized based on risk and fixed as quickly as possible.
Technology
You don’t have to manage web application security manually. That would be impossible. There are a host of security tools to help automate the application security process.
Pre-production
The first step is the automated testing of the application from the code to deployment. There are three technologies used to find bugs before production:
- Static Application Security Testing (SAST) scans application code to find vulnerabilities.
- Dynamic Application Security Testing (DAST) launches real-world attacks against a running instance to catch what SAST might miss or can’t find, such as configuration errors.
- Interactive Application Security Testing (IAST) uses automated functional tests to exercise the application’s security and find weaknesses attackers might exploit.
All of these tools help to find security bugs before they reach production.
Production
However, even with all of the automated testing in place, something might make it through. So another suite of tools has appeared to protect applications in production.
Web application firewalls (WAFs) and their Next-Gen counterparts intercept traffic coming into a web application and scan it for patterns indicating an attack. These attacks are then blocked before they can do damage.
Runtime Application Self-Protection (RASP) tools live within the application and change application behavior in real-time to prevent attacks from working.
The proliferation of APIs has increased the attack surface of many web applications and requires a deeper understanding of APIs and business logic than WAFs and RASPs can provide. Attackers are changing their tactics. New and advanced application and API security platforms such as Traceable are needed to properly protect modern cloud-native applications. These tools stop attacks against your APIs and microservices in real-time and show you which services need your attention.
Throughout Product Lifecycle
The intersection between people, processes, and technology gives you the complete web application security package. Tools are powerful, but the human touch is necessary. A mixture of both is the key to success.
Technology helps the vulnerability management process by consolidating test results for all of an organization’s assets. Some tools are scanners that then store and manage the lifecycle of issues they find. But it’s often helpful to “get a second opinion” and use other programs that may find different vulnerabilities. Then you can use result consolidation tools like ThreadFix and OWASP DefectDojo so all scans and vulnerabilities found via threat modeling or penetration testing can be together in one place.
Does Adding Security Hurt the User Experience?
The topic of user experience often rears its head when people think of security. Does security automatically mean a reduced user experience?
Well, yes and no. There is always a tug of war between user experience and security, but many companies find ways to meet in the middle.
Look at your mobile phone. If there’s no lock screen, then it’s effortless to use. However, nothing stops another person from taking it and using it to pay for their new 65-inch TV. Add a requirement to enter a 30-character password and then navigate to a website to get a code to enter for 2-factor authentication, and the phone is practically useless. There’s a tradeoff.
Companies like Apple have worked tirelessly to find ways to give users security and usability at the same time. Face ID and Touch ID work well, but you have to enter the passcode every once in a while to make sure it’s you. However, this added bit of security doesn’t degrade the overall user experience.
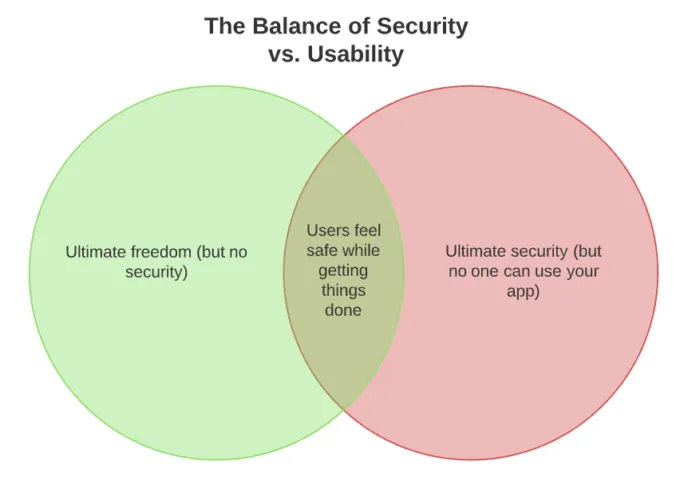
You’ve probably looked at 5 Venn diagrams today, but we’ll ask you to look at one more. Try to find the security level where your users feel safe but don’t feel like they’re entering Fort Knox every time they try to accomplish something on your site.
How Do I Learn More About Web Application Security?
Web application security is a large topic that takes years to master. But there are some great resources you can use to get up to speed.
Software Engineers
Open Web Application Security Project (OWASP)
Security Engineers
Security Now! Podcast
HackerOne’s Hacktivity Feed
PortSwigger Web Security Academy
HackerOne Hacker 101
OWASP
Executives and Team Leaders
OWASP Software Assurance Maturity Model (SAMM)
OWASP Security Knowledge Framework
CSO Online
Wrapping Up
Developing strong application security practices is the best investment you can make to secure your web applications. They aren’t going away -- they’re growing and becoming more critical each year. A deciding factor in the success or failure of companies is how well they protect customer data. Take the first step to success today, learn how to secure your web applications.
If you want to see some advanced web application security in action check out our recorded demo of Traceable Defense AI in action.
The Inside Trace
Subscribe for expert insights on application security.
.avif)



