What is Zero Trust in the Cybersecurity Executive Order


The Executive Order
The president of the United States, Joseph R. Biden, signed the Executive Order on improving the Nation’s Cybersecurity on May 12 2021. Given the recent spate of cyber attacks from the Solarwinds attack to the recent ransomware cyber-attack on the Colonial Pipeline, this order indicates the gravity of the situation and the US administration’s resolve to tackle them proactively.
The Solarwinds attack was launched from inside the U.S. on servers the attackers had rented from providers like Amazon and GoDaddy. This allowed the attackers to slip past National Security Agency’s early warning systems because the NSA is not allowed to conduct surveillance inside the United States.
"We did a detailed study of SolarWinds and it showed that we have major work to do to modernize our cybersecurity ... to reduce the risk of this happening again," Anne Neuberger, the deputy national security adviser for cyber and emerging technology at the White House had mentioned to NPR at the time, indicating firm actions would follow.
Threats impacting government and other establishments have been rampant in recent times and are not restricted to the United States alone, as we see from the report from the Center for Strategic and International studies.
There are organizations like the National Cybersecurity Alliance which have been focused on keeping sensitive information safe online and encouraging a culture of cybersecurity. The current executive order reinforces that these efforts need to be further accelerated to protect the nation’s critical assets as the nature and ramifications of these cyberattacks have gone up substantially.
Some key mandates in the executive order
Zero trust architecture
As migration to cloud technology increases, zero trust architecture should be adopted. The Cybersecurity and Infrastructure Security Agency (CISA) shall modernize its current cybersecurity programs, services, and capabilities to be fully functional with cloud-computing environments with zero trust architecture.
Baseline security standards for development of software
Improve the security of software by establishing baseline security standards for development of software sold to the government, including requiring developers to maintain greater visibility into their software and making security data publicly available.
Coordinated and centralized cataloging of incidents and responses
The Federal Government’s Playbook for Responding to Cybersecurity Vulnerabilities and Incidents will be standardized to ensure coordinated and centralized cataloging of incidents and tracking of agencies’ progress toward successful responses.
Enhanced Software Supply Chain Security
Implement more rigorous and predictable mechanisms for ensuring that products function securely, and as intended.
Zero Trust Architecture
The remainder of this blog will focus on zero trust architecture which is one of the building blocks for a comprehensive security architecture. There will be additional blogs on other topics from the executive order to highlight their significance.
Zero Trust is a security model that works on the premise that threats are omnipresent in different parts of the application and infrastructure stack. Zero trust relies on continuous verification via information from disparate sources to ensure that users and services are indeed who they claim to be and have the right privileges to access relevant resources. Different aspects of zero trust span across the dimensions outlined below, ranging from users, to applications, to the data they access.
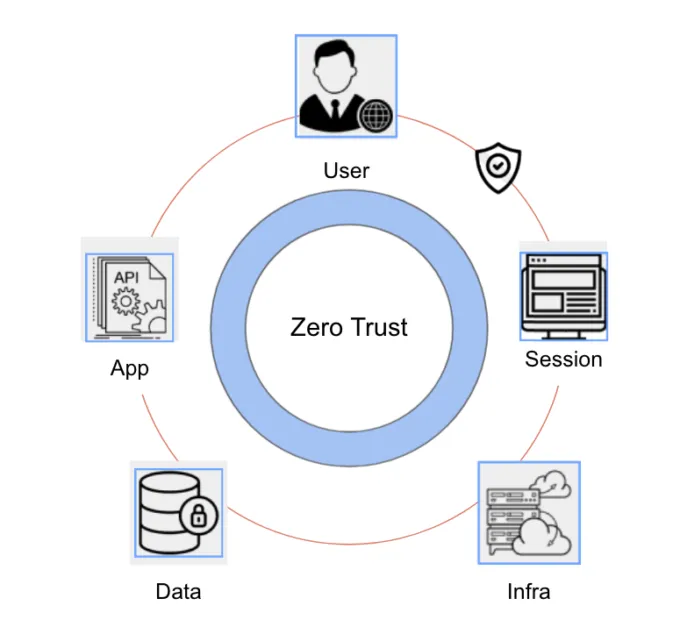
User trust
User trust is one of the key components of zero trust architecture as all users need to be considered as potential threats and access to data and resources need to be restricted until they can be authenticated and their access to relevant resources is authorized. In API security user attribution by the correct mechanisms is important to have a clear demarcation between trusted and untrusted users. These mechanisms range from SAML integration with identity providers like Okta, to users' identities being verified against Google, Github, etc.
Application trust
Applications are developed and deployed these days using cloud native approaches and have their own attack surfaces which need to be protected from malicious users and bots. With identity being outsourced in newer application stacks, the notion of trust must be extended to services and accounts. API’s are becoming more prominent as an application access mechanism and the notion of trust extends to who (users or machines) is accessing the API’s with the relevant authentication and authorization mechanisms such as API keys and Oauth.
Session trust
Session trust is an extension of application and user trust in some ways, as understanding exactly where a session of HTTP transactions begins and ends is important to baseline application traffic and map them to relevant users accessing the specific applications and API’s.
Data trust
The quote “Data is the new oil.” is credited to Mathematician Clive Humby and it is more true now than ever before. With large amounts of user data being stored by different enterprise companies, especially in SAAS based applications, it is becoming increasingly important to ensure sensitive data is protected both at rest and while in motion. On the data trust side it is important to ensure that sensitive information is only accessed by the relevant API’s and users, and having end to end traceability of the data access is key.
Infrastructure trust
Zero Trust framework for securing infrastructure entails ensuring workloads are monitored and customers are alerted when there is anomalous behavior. As with other categories, identity forms the foundation as workloads need to be assigned an identity consistently. Human access to cloud resources should be provisioned Just-In-Time with relevant automation.
Team Sport
In summary, the executive order has reiterated the importance of several key cybersecurity considerations, one of which is zero trust architecture. This is a big step forward towards securing our nation from cyber attacks, but it is ultimately the responsibility of the Government, private/public companies, and security vendors to collectively embrace these concepts to help ensure cyber attacks and data breaches are dealt with effectively.
About the Author
Sudeep Padiyar is a Product Management leader at Traceable and a soon-to-be regular contributor to The Inside Trace.
The Inside Trace
Subscribe for expert insights on application security.
.avif)

