Why Web App Firewalls Aren’t Protecting Your Cloud-Native Apps


You’ve got it covered, right?
Your web application firewall (WAF) is humming at the edges of your network, faithfully blocking malicious attacks before they can do any harm.
Better yet, it’s a Next-generation WAF (NG-WAF). It consists of signatures, rules, and a sprinkle of machine learning to protect your applications (and user data) from harm.
Yeah, right.
You’re a security expert. You don’t take anything at face value. How do you know for sure your applications are protected?
And what if you have cloud-native applications -- microservices, HTTP requests flying around, multiple touchpoints for each user request? Can an NG-WAF protect all of these apps from external and internal attacks?
We’ve discovered the answer. Let’s take a look at what NG-WAFs do well, what they struggle with, and whether a solution makes up for their gaps.
The Challenge of Traditional WAFs
According to OWASP:
A "web application firewall (WAF)" is an application firewall for HTTP applications. It applies a set of rules to an HTTP conversation. Generally, these rules cover common attacks such as Cross-site Scripting (XSS) and SQL Injection.
Modern applications are more transparent than traditional web applications. Focusing on speed and agility of development -- Continuous-Integration, Continuous-Delivery (CICD), and DevOps replacing the waterfall development model -- developers tend to use open-source projects to save development time and cost.
This transparency, ease of access, and incredible detail in documentation make the modern applications attractive targets. The frequent changes in applications make it almost impossible to detect and secure every vulnerability.
WAFs have added new features over the years, but the backbone of their detection still lies in their signatures or rules. The question is: have WAFs indeed adapted to the needs of cloud-native applications?
Applications have evolved from massive monoliths to microservices and distributed architectures. They now live virtually in any combination of public, private, or hybrid cloud. The new challenges and threats brought on by distributed architectures have given rise to the NG-WAFs.
Network firewalls underwent a similar transition, where the Next-Generation Firewalls (NGFWs) introduced a new perspective of looking at firewall traffic with deep packet inspection and attack-centric detection models.
The next generation WAFs have been frequently defined with three principal characteristics:
- Detection is based on the application and the attacker's behavior.
- Going beyond signatures to identify anomalies and fundamental attacker actions.
- Cloud-native deployment supporting various cloud platforms, APIs, and microservices architecture
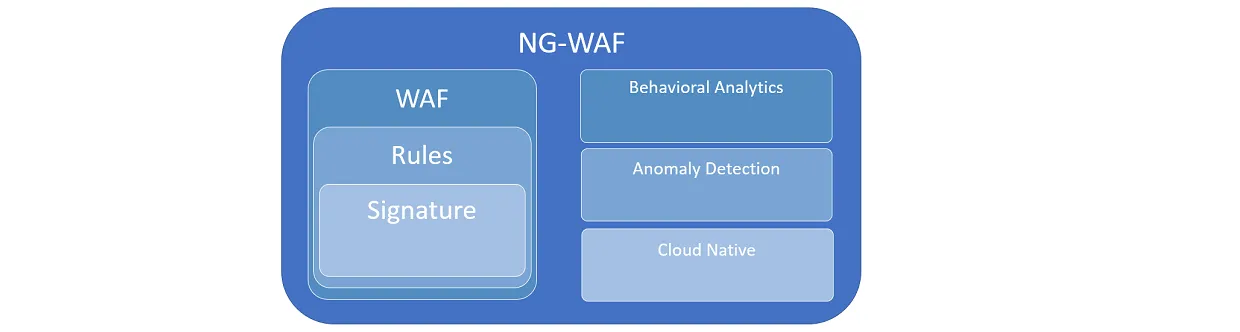
What NG-WAFs Solve
NG-WAFs propose to solve the new problems introduced by changing application architectures.
How well have they done? Let’s start by reviewing what NG-WAFs do well.
Increased Cost to Attackers
Attackers have a distinct advantage -- they don’t play by the rules.
We live in an age when you can connect almost any device in your home to the internet. Unfortunately, many IoT devices don’t take security measures, which means attackers are salivating at the opportunity.
Malicious actors try to mask their origin and evade detection using an army of “bots.” Yes, they’re attacking you with DVRs, cameras, and lightbulbs.
NG-WAFs take a fresh approach of correlating such behavior to detect the attackers and block them, thus increasing the cost for attackers and partly deter the script kiddies.
Layered Protection: The In-depth Defense
Defense in Depth increases system security by using a multi-layered approach with intentional redundancies. It’s commonly referred to as the "castle approach" because it mirrors a medieval castle's layered protection. If one layer fails, another is waiting to take its place.
NG-WAFs have evolved to protect at multiple levels, including the traditional perimeter and the newer approach of embedding alongside the applications. These layers make an attacker’s job much more difficult and expensive.
Machine Learning and Behavioral Analytics with Automated Policy Learning
NG-WAFs aggregate detection from multiple applications to understand attackers from a broader perspective to contextually score them. Using machine learning and behavior analytics on the aggregated data, NG-WAFs automatically disable signatures that would trigger false positives and update the application policies accordingly.
Virtual patching
You ideally want to identify and fix every vulnerability found in your code. But real-world business situations dictate that not all vulnerabilities will be fixed quickly or at all.
A few NG-WAFs support virtual patching to prevent attackers from exploiting critical vulnerabilities until an official fix is available.
Cloud-native Support
NG-WAFs now support deployment in a public, private, or hybrid cloud. The NG-WAFs automatically integrate with a containerized approach to scale security natively and elastically. They distribute nodes all over the world to maximize coverage without increasing latency.
What NG-WAFs Have Failed to Solve
NG-WAFs have made strides in securing applications. They’ve used defense-in-depth to make successful attacks increasingly tricky to pull off.
They’ve incorporated new architectures and virtual patching to match the pace and style of current app development. But they haven’t solved every problem.
Let’s look now at what NG-WAFs are missing that may open up holes in your security.
Motivated Attackers Can Bypass NG-WAFs
WAFs introduce obstacles for hackers and penetration testers by making vulnerability finding and exploitation more resource-intensive. However, an experienced hacker or a researcher with enough motivation would probably be able to find ways to bypass it.
When the application use case becomes complex, it may demand disabling many defenses that produce a higher false positive rate. The more complex a web application is, the bigger its attack surface, and the easier it is to find a bypass for it.
NG-WAFs Are Vulnerable to Use Case Exploitation
The same application deployed in different contexts exhibits different behavior. Requests that are harmful for one application may be perfectly normal for the other as user behavior varies for each case.
NG-WAFs do not have a complete picture of application usage -- they cannot detect the business use case. The attack patterns stay hidden within regular traffic and nested protocols. Eventually, the attacker can tune himself to the business traffic and bypass the NG-WAFs resulting in a window of vulnerability and delay in breach detection. Straightforward implementations for detecting such use case exploitation often result in a high rate of false positives and false negatives. Further, customers rarely use all of the available features and rules in modern NG-WAFs.
Machine Learning and Behavioral Analysis Are Limited to Perimeter Defense.
NG-WAFs have evolved from WAFs and base themselves on a “perimeter defense” model -- it guards only against malicious traffic originating outside the network. However, this model fails if an attack comes from within – a common occurrence given the wide variety of ways users can connect to an internal network.
The new "stay at home" normal and increased risk of insider threats has led enterprises to adopt the Zero Trust model. It is essential to monitor the external traffic along with the internal flow and state of the applications.
Missing Runtime Protection
Malicious hackers are attacking all the application stack tiers, be it web, memory, or database. By design, NG-WAFs are limited at the edge of the application module and cannot protect the application at runtime. With this knowledge, the attacker could also circumvent the virtual patch defenses once the vulnerability is known to them by altering their attack method or mingling with the business traffic.
Monitoring blind spots
Monolithic frameworks base the visibility into the application on logging frameworks. Want to know what’s happening? Only one directory to check.
Modern applications built on microservices and serverless introduce advantages to application development, but there's also the cost of reduced visibility. You can monitor each service individually, but one can quickly lose sight of the global system behavior.
A single request to the modern application can create a chain of calls behind the scenes. What appears simple can sometimes be incredibly complicated. For example, take a look at what happens inside Netflix when you hit play during your latest binge.
This call chain generates a massive amount of data along its flow path. External applications have trouble ingesting it all. Instead of solving this problem, most NG-WAFs limit the amount of data they can capture and process, introducing blind-spots the attackers can leverage to bypass them.
How to Protect Cloud-Native Applications
Cloud-native microservice architectures introduce drastic benefits but are also challenging to defend. While NG-WAFs have made some strides but they still fall short in several crucial areas. To comprehensively protect your cloud-native apps you should look for a solution that seamlessly provides both security observability and intelligent threat detection. Look for solutions that offer:
- end to end distributed tracing and visibility, increasing the accuracy and depth of attack detection without extra overhead
- features that establish baselines for user behavior, API logic, and data flow to identify anomalies
- the ability to block business use case abuses, insider attacks, and threat actors, even in distributed systems
- visibility that provides a complete picture of how data (especially sensitive business and personal data) moves throughout your application so you can see problem areas before they become exploits
- discovery and protection of the complete eco-system of your microservices
If you’d like to learn more about TraceableAI you can view a recorded demo of Traceable in action.
The Inside Trace
Subscribe for expert insights on application security.
.avif)

